Database Management System: Unit III: Transactions
Two marks Questions with Answers
Transactions - Database Management System
A transaction can be defined as a group of tasks that form a single logical unit.
Two Marks Questions with Answers
Q.1 What is a transaction? AU: May-04, Dec.05
Ans: A
transaction can be defined as a group of tasks that form a single logical unit.
Q.2 What does time to commit mean? AU: May-04
Ans:
• The COMMIT command is used to save permanently any
transaction to database.
• When we perform, Read or Write operations to the
database then those changes can be undone by rollback operations. To make these
changes permanent, we should make use of commit
Q.3 What are the various properties of transaction
that the database system maintains to ensure integrity of data. AU: Dec.04
OR
Q.4 What are ACID properties? AU:
May-05,06,08,13,15, Dec-07,14,17
Ans:
In a database, each transaction should maintain ACID property to meet the
consistency and integrity of the database. These are
(1) Atomicity (2) Consistency (3) Isolation (4) Durability
Q.5 Give the meaning of the expression ACID
transaction. AU: Dec.08
Ans:
The expression ACID transaction represents the transaction that follows the
ACID Properties.
Q.6 State the atomicity property of a transaction. AU: May-09,13
Ans:This property states that each transaction
must be considered as a single unit and must be completed fully or not
completed at all.
No transaction in the database is left half completed.
Q.7 What is meant by concurrency control ? AU:
Dec.15
Ans:
A mechanism which ensures that simultaneous execution of
more than one transactions does not lead to any database inconsistencies is
called concurrency control mechanism.
Q.8 State the need for concurrency control. AU: Dec.17
OR
Q.9 Why is it necessary to have control of
concurrent execution of transactions? How is it made possible? AU: Dec.-02
Ans:
Following are the purposes of concurrency control-
• To ensure isolation
• To resolve read-write or write-write conflicts
• To preserve consistency of database
Q.10 List commonly used concurrency control
techniques. AU: Dec.11
Ans: The commonly used concurrency control
techniques are -
i) Lock
ii) Timestamp
iii) Snapshot Isolation
Q.11 What is meant by serializability? How it is
tested? AU: May-14,18, Dec.-14,16
Ans.:
Serializability is a concept that helps to identify which non serial schedule
and find the transaction equivalent to serial schedule.
It is tested using precedence graph technique.
Q.12 What is serializable schedule? AU:
May-17
Ans.: The schedule
in which the transactions execute one after the other is called serial
schedule. It is consistent in nature. For example : Consider following two
transactions T1 and T2

All the operations of transaction T1 on data items A and then
B executes and then in transaction T2 all the operations on data
items A and B execute. The R stands for Read operation and W stands for write
operation.
Q.13 When are two schedules conflict equivalent? AU: Dec.08
Ans.: Two
schedules are conflict equivalent if :
• They
contain the same set of the transaction.
• every pair of conflicting actions is
ordered the same way.
For example -
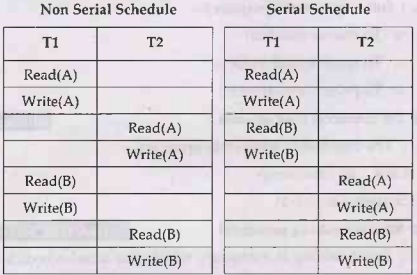
Schedule S2 is a serial schedule because, in
this, all operations of T1 are performed before starting any
operation of T2. Schedule S1 can be transformed into a
serial schedule by swapping non-conflicting operations of S1.
Hence both of the above the schedules are conflict equivalent.
Q.14 Define two phase locking. AU: May-13
Ans.: The two
phase locking is a protocol in which there are two phases:
i) Growing Phase (Locking Phase): It is a phase in which the transaction may obtain locks but does not
release any lock.
ii) Shrinking Phase (Unlocking Phase): It is a phase in which the
transaction may release the locks but does not obtain any new lock.
Q.15 What is the difference between shared lock and
exclusive lock? AU: May-18
Ans.:

Q.16 What type of lock is needed for insert and
delete operations. AU: May-17
Ans.:
The exclusive lock is needed to insert and delete operations.
Q.17 What benefit does strict two-phase locking
provide? What disadvantages result? AU:
May-06,07, Dec.07
Ans.:
Benefits:
1. This ensure that any data written by an uncommitted
transaction are locked in exclusive mode until the transaction commits and
preventing other transaction from reading that data.
2. This protocol solves dirty read problem.
Disadvantage:
1. Concurrency is reduced.
Q.18 What is rigorous two phase locking protocol ? AU: Dec.-13
Ans.: This is
stricter two phase locking protocol. Here all locks are to be held until the
transaction commits.
Q.19 Differentiate strict two phase locking and
rigourous two phase locking protocol. AU:
May-16
Ans. :
• In Strict two phase locking protocol
all the exclusive mode locks be held until the transaction commits.
• The rigourous two phase locking protocol is
stricter than strict two phase locking protocol. Here all locks are to be held
until the transaction commits
Q.20 Define deadlock. AU: May-08,09,14
Ans.:
Deadlock is a situation in which when two or more transactions have got a lock
and waiting for another locks currently held by one of the other transactions.
Q.21 List four conditions for deadlock. AU: Dec-16
Ans.:
1. Mutual exclusion condition
2. Hold and wait condition
3. No preemption condition
4. Circular wait condition
Q.22 Why is recovery needed? AU: May-09
Ans. :
• A recovery scheme that can restore
the database to the consistent state that existed before the failure.
• Due to recovery mechanism, there is high
availability of database to its users.
Q.23 What are states of transaction? AU: May-19
Ans.: Various
states of transaction are - (1) Active, (2) Partially Committed (3) Failed (4)
Aborted (5) Committed.
Q.24 What is meant by log based recovery?
Ans.: Log is a
most commonly used data structure for recording the modifications that can be made
to actual database.
Log based recovery is a technique in which a log of each transaction is
maintained in some stable storage so that if failure occurs then it can be
recovered from there.
Q.25 List the responsibilities of a DBMS has
whenever a transaction is submitted to the system for execution. AU: Dec.-19
Ans.: The system
is responsible for making sure that - (1) Either all the operations in the
transaction are completed successfully and effect is recorded permanently in
the database. (2) The transaction, has no effect whatsoever on the database or
on the database or on any other transaction.
Q.26 Brief any two violations that may occur if a
transaction executes a lower isolation level than serializable. AU: Dec.-19
Ans.: (1) For
non-repeatable Read the phantom read is allowed.
Database Management System: Unit III: Transactions : Tag: : Transactions - Database Management System - Two marks Questions with Answers
Related Topics
Related Subjects
Database Management System
CS3492 4th Semester CSE Dept | 2021 Regulation | 4th Semester CSE Dept 2021 Regulation
