Introduction to Operating Systems: Unit IV(b): File System
Protection
File System - Introduction to Operating Systems
User information and data is stored in the secondary storage. It is necessary to provide security from physical damage and improper access.
Protection
•
User information and data is stored in the secondary storage. It is necessary
to provide security from physical damage and improper access.
Type of Access
• Access is limited or full access of
data. User having full access can perform read, write and modify operation on
the data and information. In limited access, user only read and executes the
information.
•
Protection mechanism provides controlled access. Following are some of the aw
operation performed on the files.
1.
Read: User can read a file.
2.
Write: User can rewrite a file.
3. Delete: User can delete a file
whenever space is required.
4.
Execute:
User execute a file after loading into the main memory.
5. List: User check attributes of the
file and file/directory names.
Access Control
• Traditionally, a file object in Linux
is associated with three sets of permissions. These sets assign read (r), write
(w), and execute (x) permissions for the three user groups file owner
group, and other.
•
Nine bits are used to determine the characteristics of all objects in a Linux system. Additionally, the set user id, set group id and sticky bits can be
set for special cases.
• ACLS can be used for situations where
the traditional file permission concept does not suffice. They allow the
assignment of permissions to individual users or groups even if these do not
correspond to the owner or the owning group. Access Control Lists are a feature
of the Linux kernel.
• There are two types of ACLS : Access ACLS and default ACLs. An access ACL is the access control list for a specific file or directory. A default ACL can only be associated with a directory; if a file within the directory does not have an access ACL, it uses the rules of the default ACL for the directory. Default ACL's are optional.
•
ACL's can be configured:
1. Per user 2. Per group
3.
Via the effective rights mask
4.
For users not in the user group for the file.
Access
determination
• When
a process attempts to access a file, its effective UID is compared to the UID
that owns the file. If they are the same, access is determined by the ACL's
user permissions. Otherwise, if a matching user specific ACL entry exists,
permissions are determined by that entry in combination with the ACL mask.
•
If no specific entry is available, the file system tries to locate a valid group
related b entry that provides the required access; these entries are processed
in conjunction se with the ACL mask. If no matching entry can be found, the
other entry prevails.
NFSv4 ACL
•
The NFSv4 (Network File System - Version 4 protocol introduces a new ACL format
that extends other existing ACL formats. NFSv4 ACL is easy to work with and
introduces more detailed file security attributes, making NFSv4ACLs more
•
NFSv4 ACL's are similar to Windows ACL's in structural perspective. In both the
system, ACL stores this entity as a string.
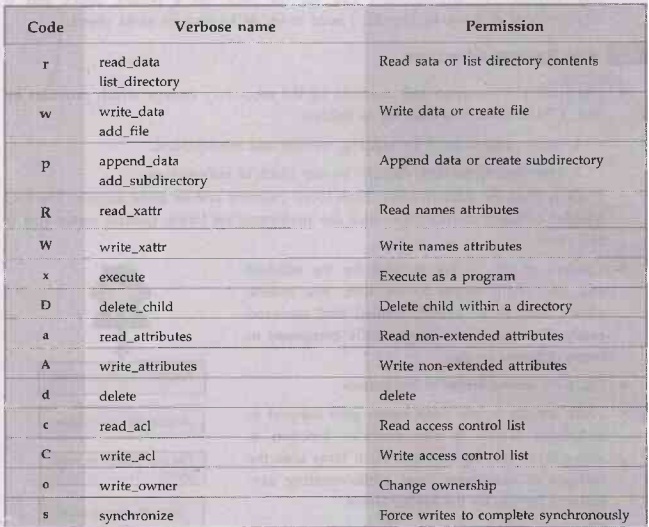
The Windows and NFSv4 permission model
is more granular than the traditional UNIX read-write-execute model.
1.
NFSv4 distinguishes permissions to create files within a directory from
permission to create subdirectories.
2. NFSv4 has a separate append
permission bit.
3.
NFSv4 has separate read and write permissions for data, file attributes,
extended attributes, and ACLs.
4.
NFSv4 controls a user's ability to change the ownership of a file through the
standard ACL.
NFSv4
file permissions
Access
Determination in NFS
• In the POSIX ACL system, the file
system attempts to match the user's identity to the single most appropriate
access control entry. The Access Control Entry (ACE) then provides a complete
set of controlling permissions for the file.
• Each NFSv4 ACE is either an "allow" ACE or a "deny" ACE. When deciding whether to allow a particular operation, the file system reads the ACL in order, processing ACEs until either all requested permissions have been allowed or some requested permission has been denied.
ACL
inheritance
• ACL inheritance is a mechanism that
lets container objects pass access control information to their child objects.
A container's child objects can be non-container objects as well as other
container objects.
• From an administrator point of view,
ACL inheritance simplifies access control management. An administrator can set
the ACL on a parent object and if inheritance is enabled, he shouldn't need to
set ACLS on each child object.
Introduction to Operating Systems: Unit IV(b): File System : Tag: : File System - Introduction to Operating Systems - Protection
Related Topics
Related Subjects
Introduction to Operating Systems
CS3451 4th Semester CSE Dept | 2021 Regulation | 4th Semester CSE Dept 2021 Regulation
