Database Management System: Unit III: Transactions
Locking Protocols
Transactions - Database Management System
One of the method to ensure the isolation property in transactions is to require that data items be accessed in a mutually exclusive manner.
Locking Protocols
AU: Dec-15,17, May-16, Marks 16
Why Do We Need Locks?
• One of the method to ensure the
isolation property in transactions is to require that data items be accessed in
a mutually exclusive manner. That means, while one transaction is accessing a
data item, no other transaction can modify that data item.
• The most common method used to
implement this requirement is to allow a transaction to access a data item only
if it is currently holding a lock on that item.
• Thus the lock on the operation is
required to ensure the isolation of transaction.
Simple Lock Based Protocol
• Concept of Protocol: The lock based
protocol is a mechanism in which there is exclusive use of locks on the data
item for current transaction.
• Types of Locks: There are two types of locks used -
i) Shared Lock: The shared lock is used for reading data items only. It is
denoted by Lock-S. This is also called as read lock.
ii) Exclusive Lock: The exclusive lock is used for both read and write
operations. It is denoted as Lock-X. This is also called as write lock.
• The compatibility matrix
is used while working on set of locks. The concurrency control manager checks
the compatibility matrix before granting the lock. If the two modes of
transactions are compatible to each other then only the lock will be granted.
• In a set of locks may consists of shared or
exclusive locks. Following matrix represents the compatibility between modes of
locks.
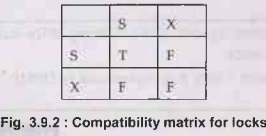
Here T stands for True and F stands for False. If the control manager
get the compatibility mode as True then it grant the lock otherwise the lock
will be denied.
• For example: If the transaction T1 is holding a shared lock in data item
A, then the no control manager can grant the shared lock to transaction T2
as compatibility is True.
But it cannot grant the exclusive lock as the compatibility is false. In
simple words if transaction T1 is reading a data item A then same
data item A can be read by another transaction T2 but cannot be written
by another transaction.
• Similarly if an exclusive lock (i.e.
lock for read and write operations) is hold on the data item in some
transaction then no other transaction can acquire Share or exclusive lock as the
compatibility function denotes F. That means of some transaction is writing a
data item A then another transaction can not read or write that data item A.
Hence the rule of thumb is
i) Any number of transactions can hold shared lock on an
item.
ii) But exclusive lock can be hold by only one
transaction.
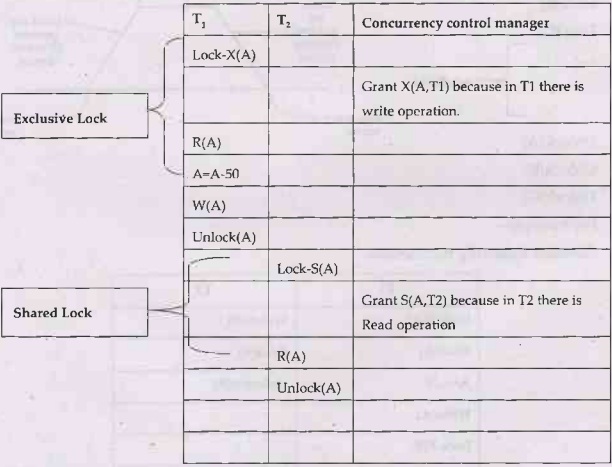
• Example of a schedule denoting
shared and exclusive locks:
Consider following schedule in which initially A=100. We deduct 50 from A in T,
transaction and Read the data item A in transaction T2. The scenario can be
represented with the help of locks and concurrency control manager as follows:
Review Questions
1.State and explain the lock based concurrency
control with suitable example.
AU: Dec-17, Marks 13, May-16, Marks 16
2. What is Concurrency control? How is implemented
in DBMS? Illustrate with suitable example.
AU: Dec-15, Marks 8
Database Management System: Unit III: Transactions : Tag: : Transactions - Database Management System - Locking Protocols
Related Topics
Related Subjects
Database Management System
CS3492 4th Semester CSE Dept | 2021 Regulation | 4th Semester CSE Dept 2021 Regulation
