Database Management System: Unit V: Advanced Topics
Encryption and Public Key Infrastructures
Advanced Topics - Database Management System
Cryptology is a technique of encoding and decoding messages, so that they cannot be understood by anybody except the sender and the intended recipient.
Encryption and Public Key
Infrastructures
Cryptology is a technique of encoding and decoding messages,
so that they cannot be understood by anybody except the sender and the intended
recipient.
There are various encoding and decoding schemes which are
called as encryption schemes. The sender and recipient of the message decide on
an encoding and decoding scheme and use it for communication.
The process of encoding messages is known as encryption. The
sender sends the original text. The original text called plaintext, The
encrypted form of plaintext it is called as ciphertext. This encrypted text
travel through the network. When it reaches at the receiving computer, the
recipient understands the meaning and decodes the message to extract the
correct meaning out of it. This process is called as decryption.
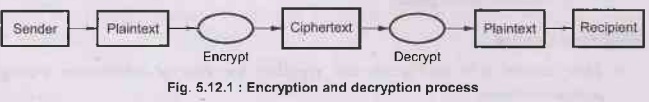
The sender applies the encryption algorithm and recipient applies the
decryption algorithm. Both the sender and the receiver must agree on this
algorithm for any meaningful communication. The algorithm basically takes one
text as input and produces another as the output. Therefore, the algorithm
contains the intelligence for transforming message.
For example: If we want to send some message through an e-mail and we
wish that nobody except the friend should be able to understand it. Then the
message can be encoded using some intelligence. For example if the alphabets A
to Z are encoded as follows-

That means last three letters are placed in reverse order and then first
three letters are in straight manner. Continuing this logic the A to Z letters
are encoded. Now if I write the message
"SEND SOME MONEY"
it will be
QBSA QRTB TRSBN
This coded message is called cipher text.
There are variety of coding methods that can be used.
Types of Cryptography
There are two types encryption schemes based in key used for encryption
and decryption.
1. Symmetric key encryption: It is also known as secret key
encryption. In this method, only one key is used. The same key is shared by
sender and receiver for encryption and decryption of messages. Hence both
parties must agree upon the key before any transmission begins and nobody else
should know about it. At the sender's end, the key is used to change the
original message into an encoded form. At the receiver's end using the same key
the encoded message is decrypted and original message is obtained. Data
Encryption Standard (DES) uses this approach. The problem with this approach is
that of key agreement and distribution.
2. Asymmetric key encryption: It is also known as public key
encryption. In this method, different keys are used. One key is used for
encryption and other key must be used for decryption. No other key can decrypt
the message-not even the original key used for encryption.
One of the two keys is known as public key and the other is
the private key. Suppose there are two users X and Y. The
• X wants to send a message to Y. Then
X
will convey its public key to Y but the private key of X will be known to X
only.
• Y should know the private key of Y and X should
know the Y's public key.
When X and Y wants to communicate:m
1. If X wants to send a message to Y, then first of all X encrypts the
message using Y's public key. For that purpose it is necessary that X knows the
Y's public key.
2. X then sends this encrypted to Y.
3. Now using Y's private key, Y decrypts X's message. Note that only Y
knows his private key. It is not possible for Y to decrypt the message using
X's public key.
4. When Y wants to send a message to X then using X's public key Y will
encrypt the message and will send the encrypted message to X. On the other
hand, X will use its own private key to decrypt this message. Here again Y will
not know the private key of X.
Digital Signature
A digital signature is a mathematical scheme for demonstrating the
authenticity of a digital message or document. If the recipient gets a message
with digital signature then he believes that the message was created by a known
sender.
Digital signatures are commonly used for software distribution,
financial transactions, and in other cases where it is important to detect
forgery or tampering.
When X and Y wants to communicate with each other
1. X encrypts the original plaintext message into ciphertext by using
Y's public key.
2. Then X executes an algorithm on the original plaintext to calculate a
Message Digest, also known as hash. This algorithm takes the original plaintext
in the binary format, apply the hashing algorithm. As an output a small string
of binary digits gets created. This hashing algorithm is public and anyone can
use it. The most popular message digest algorithms are MD5 and SHA-1. X
encrypts the message digest. For this, it uses its own private key.
3. X now combines the ciphertext and its
digital signature (i.e encrypted message digest) and it is sent over the
network to Y.
4. Y receives the ciphertext and X's digital signature. Y
has to decrypt both of these. Y first decrypts ciphertext back to plaintext.
For this, it uses its own private key. Thus, Y gets the message itself in a
secure manner.
5. Now to ensure that the message has come from the intended sender Y
takes X's digital signature and decrypts it. This gives Y the message digest as
was generated by X. The X had encrypted the message digest to form a digital
signature using its own private key. Therefore, Y uses X's public key for
decrypting the digital signature.
6. Hash algorithm to generate the message digest is public.
Therefore, Y can also use it.
7. Now there are two message digests one created by X and other by Y.
The Y now Anon simply compares the two message digests. If the two match, Y can
be sure that the message came indeed from X and not from someone else.
Thus with digital signature confidentiality,
authenticity as well as message integrity is assured.
The other important feature supported by digital signature is
non-repudiation. That is, a sender cannot refuse having sent a message. Since
the digital signature requires the private key of the sender, once a message is
digitally signed, it can be legally proven that the sender had indeed sent the
message.
Review Question
1. Explain in brief the concept of digital
signature.
Database Management System: Unit V: Advanced Topics : Tag: : Advanced Topics - Database Management System - Encryption and Public Key Infrastructures
Related Topics
Related Subjects
Database Management System
CS3492 4th Semester CSE Dept | 2021 Regulation | 4th Semester CSE Dept 2021 Regulation
